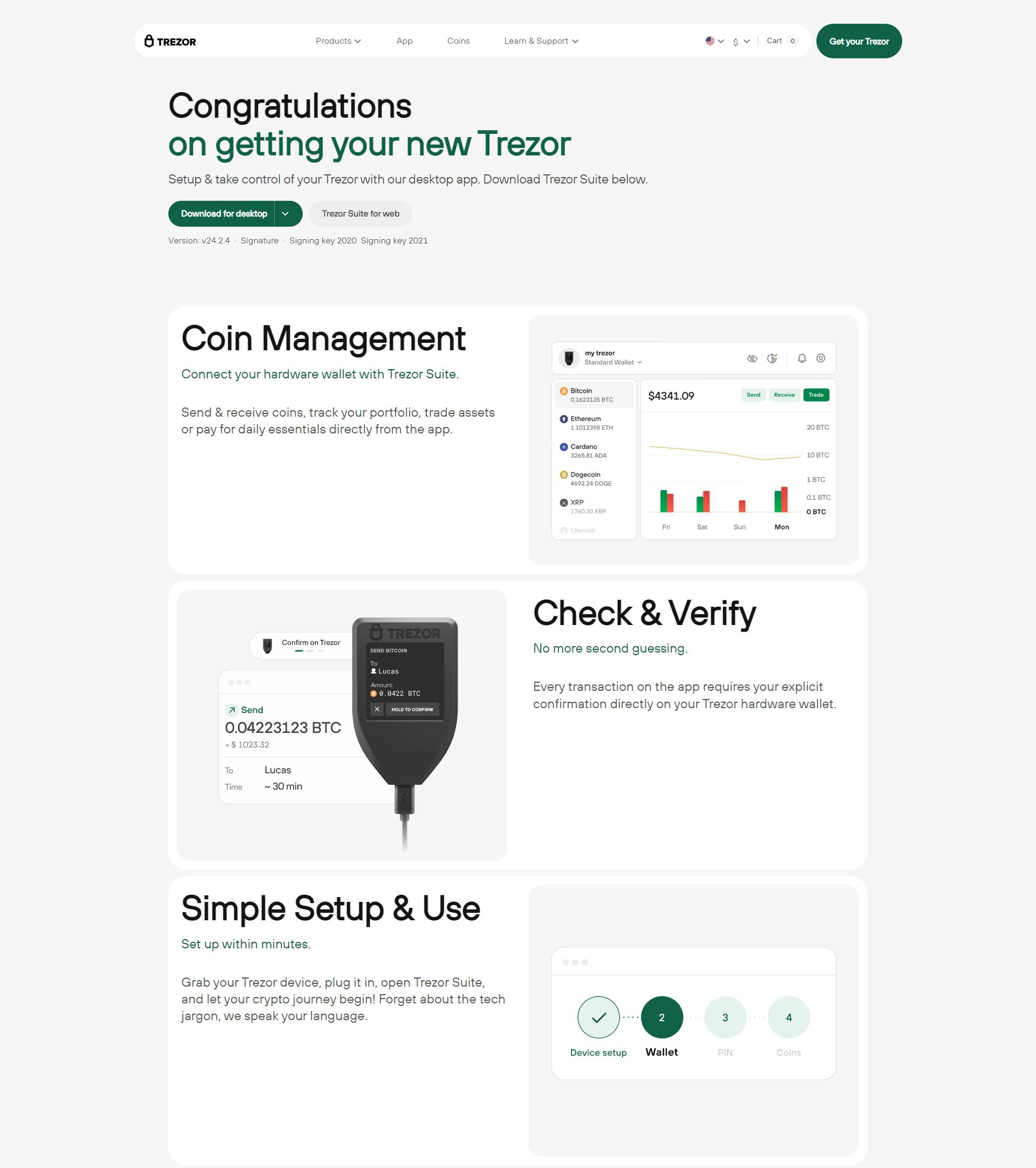
Introduction to Trezor: Why It’s a Game-Changer for Crypto Security
In the world of cryptocurrency, securing your assets is of utmost importance. With the increasing frequency of hacks, phishing attempts, and scams, protecting your private keys is critical. Trezor, a hardware wallet created by SatoshiLabs, offers one of the most secure ways to store your cryptocurrency. This step-by-step guide will help you set up your Trezor device and start managing your crypto with peace of mind.
What Is Trezor?
Trezor is a leading hardware wallet that allows users to store their cryptocurrencies offline, making them less vulnerable to hacking and online threats. With Trezor, your private keys are stored in a secure, physical device, ensuring that even if your computer is compromised, your assets remain safe. It's one of the most popular and trusted brands in the cryptocurrency space.
Why Use a Hardware Wallet Like Trezor?
- Offline Storage: Your private keys never leave the device, meaning they cannot be hacked through the internet.
- Multi-Currency Support: Trezor supports a wide range of cryptocurrencies including Bitcoin, Ethereum, and Litecoin.
- User-Friendly: Trezor’s setup and usage are simple enough for beginners while providing advanced features for experienced users.
- Security Features: Trezor offers two-factor authentication, PIN protection, and passphrase support for added security.
How to Set Up Your Trezor Wallet
Getting started with your Trezor wallet is easy. Follow these simple steps to set up your device and begin securing your crypto assets:
Step 1: Unbox Your Trezor
Inside the Trezor box, you will find the device, a USB cable, and a recovery seed card. The recovery seed card is extremely important—this is your backup in case you lose your device or forget your PIN. Keep it in a safe place.
Step 2: Connect Trezor to Your Computer
Plug the Trezor device into your computer using the USB cable provided. The screen on your Trezor will display a welcome message and prompt you to visit the official Trezor website for further instructions.
Step 3: Install Trezor Bridge
Trezor requires a small piece of software called Trezor Bridge to be installed on your computer. This software allows your Trezor device to communicate with your web browser securely. Once installed, you’ll be able to interact with your wallet using the Trezor web interface.
Step 4: Set Up a PIN Code
For security purposes, you’ll need to set up a PIN code. This PIN will be required every time you access your Trezor wallet. Choose a PIN that’s both secure and memorable, and keep it safe.
Step 5: Write Down Your Recovery Seed
During the setup process, Trezor will generate a recovery seed—a list of 12 to 24 words that will allow you to restore your wallet if it’s lost, stolen, or damaged. Write down the recovery seed on the card provided and store it in a safe location. Do not store it digitally, as it could be hacked.
Step 6: Begin Using Your Trezor Wallet
After completing these steps, your Trezor is ready to use. You can now send and receive cryptocurrencies, view your balance, and manage your assets with ease. If you want to add more cryptocurrencies to your Trezor, simply use the Trezor wallet interface to install the corresponding app for each coin.
Common Questions About Trezor
What happens if I lose my Trezor device?
If you lose your Trezor device, you can restore your wallet using the recovery seed that was generated during setup. As long as you have your recovery seed, you can recover your funds on a new Trezor device or any compatible wallet.
Can I use Trezor with my mobile device?
Yes, Trezor is compatible with both desktop and mobile devices. For mobile use, you can connect it to your smartphone using a USB OTG cable, and access your wallet using compatible apps like Trezor's official app or third-party wallets.
Is Trezor safe from online hackers?
Yes, because Trezor is a hardware wallet that stores your private keys offline, it is not vulnerable to online hacks or phishing attacks. As long as you keep your recovery seed safe, your funds are secure even if your computer is compromised.
Conclusion: Protect Your Crypto with Trezor
Trezor offers a simple yet highly effective way to secure your cryptocurrency assets. By setting up your Trezor device and following the best security practices, you can significantly reduce the risk of losing your funds to online threats. Remember to keep your recovery seed safe, and always verify the authenticity of your Trezor device before setting it up. Protecting your crypto has never been easier with Trezor by your side.